The technological advancements that have come with the digital age have simplified life in several ways. Their key undoing, though, is the susceptibility to breaches. That’s where cryptography comes in. It helps ensure that our data remains confidential and secure.
But as hackers refine their tactics, our defenses must also evolve. Here’s where Elliptic Curve Cryptography (ECC) fits. If implemented correctly, ECC encryption can reshape the cybersecurity landscape.
ECC combines mathematical elegance with strength to deal with the escalating cybersecurity challenges. In today’s article, we unearth the essence of Elliptic Curve Cryptography (ECC) in cybersecurity.
In this regard, we define Elliptic Curve Cryptography. We also answer the question: How does elliptic curve cryptography work? Importantly, we explain why the ECC encryption is best placed to be the pivot upon which the future of digital security hinges.
Elevating Cyber Defenses: The Promise of Elliptic Curve Cryptography
What is Elliptic Curve Cryptography?
Elliptic Curve Cryptography is a smart way to secure information. It uses the math of elliptic curves on limited fields.
The ECC algorithm offers strong security with shorter keys. This is unlike the regular methods, like those using plain Galois fields.
It’s handy for making private keys and creating random numbers. ECC can even help with encryption by mixing key-making with symmetric encryption.
ECC plays a key role in integer factorization methods for cryptography. This includes the Lenstra elliptic-curve factorization.
Lengthy RSA keys slow low-powered devices during calculations. ECC’s efficiency is also seen here; short keys provide high security without compromising speed.
ECC’s applications span domains. Governments use it for internal communications, and the Tor project ensures anonymity. Bitcoin ownership is also proven with it.
There are also the iMessage signatures that rely on ECC encryption. Also, DNS info is encrypted via ECC. Secure browsing’s authentication relies on it too.
How does ECC work?
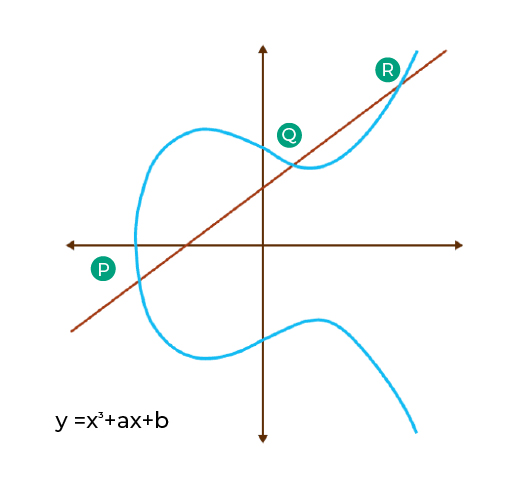
About how it actually works, Elliptical Curve Cryptography operates on a unique principle. It merges public and private keys.
The public key is visible to all, but the private key is only known, solely to the sender and receiver. This amalgamation forms the basis for encrypting and decrypting data.
The ECC algorithm facilitates strong security with compact keys, ensuring robust security. Unlike older encryption methods, ECC provides the same level of security with shorter key lengths, making it more efficient. This efficiency is especially crucial in resource-constrained environments like mobile devices.
Advantages of ECC over Traditional Cryptography
What is the main advantage of using elliptic curve cryptography over traditional public key ciphers like RSA? You may wonder. The answer lies in several compelling advantages that ECC offers over its predecessors. Here are five key benefits of Elliptic Curve Cryptography;
- Smaller Key Sizes for Equal Security: ECC can ensure the same level of security with smaller key sizes. This is its standout advantage. For instance, at high-security levels, the key sizes required for AES-256, ECC-512, and RSA-15424 are in a similar ballpark. This means ECC brings robust security without the burden of lengthy keys.
- Speedy Key Generation: Elliptical Curve Cryptography facilitates rapid key generation. ECC’s key generation efficiency allows for quicker, secure communication channels setup.
- Compact Cipher-Texts and Signatures: ECC can also produce smaller cipher texts and signatures. This not only saves storage space but also contributes to faster data transmission.
- Swift Signatures: Elliptical Curve Cryptography signatures are generated with impressive speed. These signatures can even be computed in two stages. This helps reduce latency and enhances the efficiency of the cryptographic process.
- Efficient Encryption and Decryption: The advances in elliptic curve cryptography allow for fast encryption and decryption speeds. Now, it might not outpace the inverse throughput. But, efficient performance is very notable.
ECC has seamlessly integrated into various cryptographic protocols, like SSL/TLS certificate and SSH. All these reflect its relevance in securing communication.
This integration empowers systems with enhanced security without sacrificing operational speed. The significance of ECC in securing internet communication can also not be overstated.
Data breaches and cyber threats are becoming very sophisticated. In this regard, ECC helps by providing a robust shield for sensitive information.
It strikes a remarkable balance between impregnable security and swift data transfer. This makes it a cornerstone of secure online interactions.
ECC’s compactness, speed, and security advantages are undeniable in cryptographic landscapes. It has garnered massive support from the U.S. government. This further solidifies its status as a reliable encryption method.
Real-World Applications of Elliptic Curve Cryptography
Elliptic Curve Cryptography (ECC) isn’t only theoretical. The applications of Elliptic Curve Cryptography are vast. It is the powerhouse behind many real-world applications maintaining security in digital interactions.
Let’s take HTTPS, for example. HTTPS, the padlock of online security, utilizes ECC for key exchange. When you see “https://” in your browser’s address bar, ECC is at work. It enables the secure transfer of data between your device and websites.
Read More: HTTPS vs. HTTP: Why Do You Need to Switch From HTTP to HTTPS?
ECC’s efficiency lies in its ability to generate smaller keys. It achieves this while still maintaining high security. This means quicker connections and less processing power required. These are the perfect combinations for mobile browsing.
ECC’s efficiency is a game-changer for HTTPS. It streamlines the encryption process without compromising safety.
VPN protocols that safeguard online privacy also reap the benefits of elliptic curve cryptography. ECC’s small key sizes are a boon here, too.
It doesn’t matter whether you’re accessing public Wi-Fi or browsing sensitive information. ECC-driven VPNs will secure your data while ensuring swift connections. This efficiency is especially crucial for maintaining seamless browsing experiences across various devices.
Secure messaging apps like Signal and WhatsApp also use ECC for end-to-end encryption. Here, ECC is pivotal in generating and exchanging encryption keys between users.
With the ECC algorithm, these apps achieve strong security with minimal data overhead. This ability is key for quick message delivery. When it comes to digital signatures, ECC still fits in.
Digital signatures confirm the authenticity of messages or files. ECC-based signatures are smaller than traditional methods. This translates into faster verification processes. This efficiency is essential for applications like email encryption.
In such applications, users expect quick and secure communication. Elliptical Curve Cryptography also plays a significant role in securing cryptocurrency transactions.
Bitcoin, for instance, uses ECC for generating public and private keys. This is what enables secure ownership of digital assets. ECC’s strength contributes to safeguarding these transactions against potential threats.
ECC’s Resistance against Quantum Threats
Quantum threats pose a unique challenge to traditional cryptography. These threats arise from quantum computers. Quantum computers harness the power of quantum bits or qubits.
Unlike classical bits, qubits can exist in many states simultaneously. This enables them to perform complex calculations at astonishing speeds. This computational capability threatens classical cryptographic methods.
The reason is that quantum computers can swiftly solve complex problems. They’re capable of solving problems that are almost impossible for classical computers.
Classical cryptographic methods, including RSA, are vulnerable to quantum attacks. This is due to their reliance on problems that quantum computers easily solve.
For instance, quantum computers can factor large numbers into primes with a lot of ease. This can break RSA encryption.
Also, they can solve the discrete logarithm problem exponentially faster. This can compromise systems like the Diffie-Hellman key exchange.
ECC possesses an advantage in the quantum space due to its mathematical structure. ECC’s security isn’t only dependent on problems that quantum computers speed up.
The elliptic curve discrete logarithm problem remains tough even for quantum computers. Shor’s algorithm does not offer a similar advantage against ECC.
ECC’s strength lies in the asymmetry between its mathematical operations.
Traditional computers can perform the easy multiplication of points on an elliptic curve. Yet, they struggle with the reverse operation. Reverse operation is the finding of the original points from the result. This asymmetry is essential for ECC’s security.
Quantum computers don’t provide a significant shortcut to the problem despite their prowess. In quantum, ECC’s reliance on this mathematical puzzle strengthens it against quantum attacks.
Its resistance to these attacks is stronger than RSA and classical methods. While quantum computers can break classical cryptographic systems, ECC’s underlying difficulty remains. So, ECC is considered a quantum-resistant alternative.
ECC and Post-Quantum Cryptography

Post-Quantum Cryptography (PQC) is the next frontier. It targets cryptographic methods safe from quantum computer threats.
Quantum computers can crack many traditional encryption methods. This drives the quest for new, quantum-resistant techniques.
Now, quantum computers could potentially break ECC. But, its resistance to Shor’s algorithm (a quantum attack) makes it a contender. ECC’s efficiency and effectiveness align with PQC goals.
In the quantum-resistant algorithm landscape, ECC is one of the reliable options. ECC offers security and efficiency along with lattice-based, code-based, hash-based, and multivariate-quadratic-equations. ECC’s wide use today underscores its robustness.
But, it’s prudent to tread with care. Quantum computing’s rapid strides imply potential threats. So, we must adopt techniques that stand firm even when quantum machines mature. ECC’s role, while pivotal, doesn’t stand alone; it’s part of a larger, dynamic PQC ecosystem.
The Path Ahead: ECC’s Future Impact
It is safe to say that ECC is set to reshape cybersecurity as we know it. Its efficient security advantages position it as a stalwart defender against evolving threats.
Its impact on emerging technologies, like 5G and quantum computing, is pivotal. 5G’s hyperconnectivity demands robust encryption.
Here’s another area where ECC’s compact keys and robustness stand out. Quantum computing threatens classical encryption.
But, ECC stands strong due to its inherent complexity. This is a challenge even for quantum machines. Anticipating the path ahead, ECC seems destined to underpin next-gen security strategies.
How to get an ECC SSL Certificate?
CheapSSLShop sells DigiCert Secure Site Pro products that have ECC enabled.
| ECC SSL Certificates | TYPE | Price | BUY / RENEW |
|---|---|---|---|
| DigiCert Secure Site Pro | OV | $820.00/yr. | Purchase |
| DigiCert Secure Site Pro EV | EV | $1300.00/yr. | Purchase |
Yet, SSL certificates provided by Sectigo and GlobalSign can be issued with the latest ECC algorithm technology.
Conclusion
ECC is set to play an even more pivotal role in making digital connections secure. Computing power is advancing, and new challenges are coming up. But, those challenges do not affect ECC much. Its adaptable nature positions it to tackle the future head-on.