Let us understand what is YubiKey and how it elevates the security of a code signing certificate. Also, get a step-by-step guide for creating a CSR and a key attestation Using a YubiKey token.
For any app developer or distributor, being cyber fit is a crucial shield. With the risk of data breaches looming large, its importance cannot be overstated.
A single breach cannot only spell financial disaster. It can also mean legal complications and irreparable harm to your company’s reputation. Incidentally, 60% of SMBs that suffer a cyber attack go out of business within six months. To enhance defense, the combination of Code Signing and YubiKey emerges as a key strategy.
Code Signing Certificate ensures the authenticity and integrity of the app’s code. YubiKey adds an extra layer of protection. It helps you achieve this by employing hardware-based authentication. This dynamic duo fortifies security, reassuring developers, distributors, and users alike.
What is a YubiKey?
YubiKey is a hardware-based authentication device for strengthening online security/privacy. This tiny device packs a punch with its key features. It’s a physical key that plugs into your computer or device. Its key strength? Two-factor authentication.

When you log in, you use your password and the YubiKey. This double lock keeps unauthorized persons out. The advantages are plenty.
YubiKey is nearly hacker-proof. No need to remember a bunch of passwords. You only need one key. It’s quick and simple; no fancy tech skills are required. Plus, it works across various platforms.
From apps to browsers, it can help you lock down almost anything. Now, pair YubiKey with Code Signing, and you’ve got a rock-solid duo.
Code Signing ensures app authenticity, while YubiKey guards your login details. Both unite to create a fortress of protection, where only the right keys can be used to gain entry.
Understanding the Significance of Code Signing Certificate
A Code Signing certificate is essential for software code integrity, which helps ensure the trustworthiness of software. Think of it as a digital ID card for your app. These digital certificates contain crucial identity details. They are the linchpin of software authenticity.

The mechanism is akin to a lock and key. An organization’s digital certificate marries its identity to a unique public key. This public key shares a special mathematical ‘connection’ with the private key. This partnership is known as Public Key Infrastructure (PKI).
In practice, developers use their private key to sign their code. When users run this signed code, they use the developer’s public key to confirm their identity. If it matches, the software is genuine. This process bears rich fruits for both creators and users.
With a code signing certificate, the developers gain a shield against unauthorized alterations, boosting user confidence. Users reap trust, knowing they’re interacting with legitimate software. A win-win situation for all; creators deter tampering while users escape potential hazards.
How Code Signing and YubiKey Strengthen Each Other?
Now, code Signing, as we’ve seen, confirms software authenticity using digital signatures. YubiKey is a physical device that adds muscle to this process. It acts as a safeguard for your digital keys.
Through the use of YubiKey in code signing certificates, the security is maximized and unauthorized alterations are nullified. The below key features of YubiKey enhance the security and mitigate the risks involved:
1. 2-factor authentication
2. Hardware-based security
3. Necessity of physical presence
4. Tamper-proof setup
5. Broad industry acceptance
Large tech corporations and even government agencies use YubiKey to enhance their Code Signing. Take Google, for example. The tech giant has embraced this duo for its Chrome OS to fortify user trust in their updates.
Step-by-Step Guide: YubiKey CSR Generation and Attestation
Now, to integrate YubiKey with code signing, the first thing you will need to do is buy code signing certificate and then generate CSR and attestation certificate. Here’s a streamlined guide to steer through the process once you’ve bought your code signing certificate;
- Download and Install YubiKey Manager: Get the YubiKey Manager software from Yubico’s website. Choose the right version for your operating system (Windows, Linux, macOS).
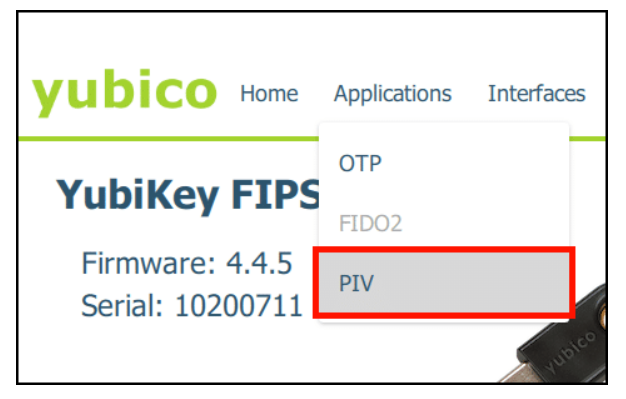
- Navigate to PIV in YubiKey Manager: Open YubiKey Manager and head to “Applications” > “PIV”.
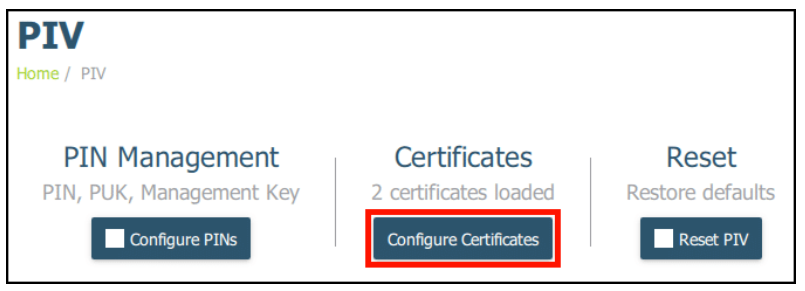
- Configure Certificates: Click “Configure Certificates”.
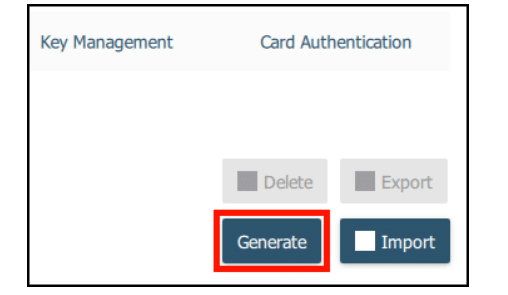
- Select Authentication (Slot 9a): Choose “Authentication (Slot 9a)” which is designated for code signing certificates.

- Generate Key Pair: Click “Generate” to create a new key pair.
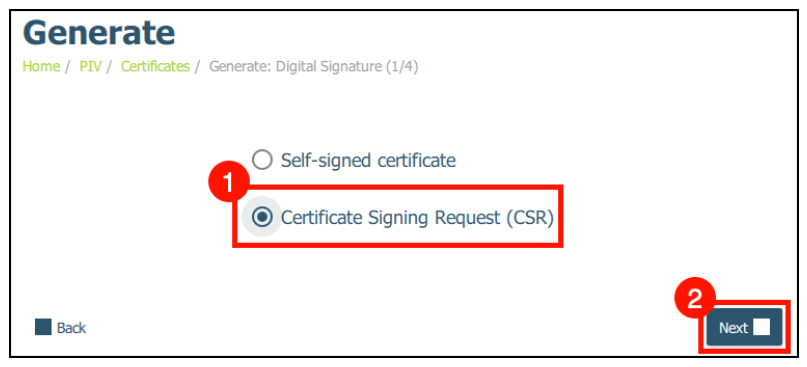
- Select CSR: Opt for “Certificate Signing Request (CSR)” and proceed.
- Choose Algorithm: Pick an algorithm from the dropdown menu. For Code Signing, go with ECCP384 due to YubiKey’s ECC algorithm support.
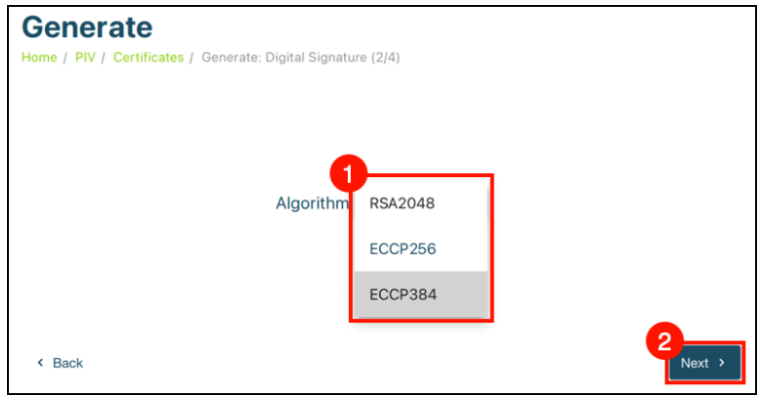
- Enter Subject Name: Provide a Subject Name for the certificate.
- Generate CSR: Click “Generate” and input;
- The directory to save the CSR.
- Your management key.
- Your PIN.
- Generate Attestation Certificate:
- On Windows: Open PowerShell as an admin and navigate to YubiKey Manager’s file path. Use the command:
.\ykman.exe piv keys attest -F PEM 9a attestation.crt
- On MacOS: Open Terminal and navigate to YubiKey Manager’s file path. Use the command:
./ykman piv keys attest -F PEM 9a attestation.crt
- On Linux: Simply run the command:
ykman piv keys attest -F PEM 9a attestation.crt
- On Windows: Open PowerShell as an admin and navigate to YubiKey Manager’s file path. Use the command:
- This attestation certificate is your proof that the private key was generated on your YubiKey.
Get Intermediate Certificate
For exporting the intermediate certificate, execute the below given command:
For Linux:
ykman piv certificates export -F PEM f9 intermediateCA.crt
For Windows:
.\ykman.exe piv certificates export -F PEM f9 intermediateCA.crt
For macOS:
./ykman piv certificates export -F PEM f9 intermediateCA.crt
Create an Attestation File
Execute below steps to create a base64-encoded attestation file:
For Linux:
cat attestation.crt intermediateCA.crt > attestation.pem
base64 attestation.pem > attestation.b64
grep -v CERTIFICATE attestation.b64
For Windows (CMD/PowerShell):
type attestation.crt intermediateCA.crt > attestation.pem
certutil -encode attestation.pem attestation.b64
findstr /v CERTIFICATE attestation.b64 > attestation.b64
And now, to complete the procedure you have to submit the following to your order configuration portal:
- CSR file (content of CSR.txt)
- base64-encoded attestation (attestation.b64)
And now, to incorporate YubiKey into the Code Signing process, you will need to install your Code Signing Certificate on YubiKey 5 FIPS.
Benefits of Code Signing with YubiKey
The CA/B Forum mandates Certificate Authorities (CAs) to incorporate Hardware Security Modules (HSMs) for issuing code signing certificates. This includes all variants from Organization Validation (OV) to Extended Validation (EV).
This move reinforces the security landscape by introducing a hardware-based safeguard against threats. It is a critical step in fortifying the integrity of code signing. YubiKey plays a pivotal role in this context. It offers benefits that enhance the security and efficacy of code signing practices. Here are the five key benefits of using YubiKey in code signing;
- Physical Hardware Safety: YubiKey operates as a standalone physical device. It has no connection to the host computer or network. Only authorized users can sign the code since the YubiKey must be physically inserted. Thus, code signing keys are shielded against potential malware or software-based attacks. The physical separation acts as a robust barrier against cyber threats, ensuring the sanctity of the code signing process.
- Two-Factor Authentication System (2FA): YubiKey employs a Two-Factor Authentication system. It demands the physical presence of the device and the user’s PIN or biometric authentication. This dual-layered approach adds an extra level of security. It grants access only to authorized personnel. By requiring physical possession of the YubiKey, it becomes nearly impossible for malicious actors to compromise or forge signatures during code signing operations. All the unauthorized code signing attempts are nullified.
- Powerful Cryptographic Security: YubiKey uses advanced cryptographic algorithms and key storage mechanisms like RSA and ECC. It guarantees swift verification to safeguard the integrity of the signed code. This robust cryptographic framework ensures that any signed code remains tamper-proof and authentic. So users trust it deeply.
- Private Key Shielding: YubiKey excels in encrypting. It is also very good at securing and managing the private keys it stores. This greatly reduces the likelihood of unauthorized access, theft, or leakage of sensitive data. The tamper-proof design of YubiKey, or any HSM (Hardware Security Module), serves as a safety net. It preserves the confidentiality of private keys – a critical component of the code signing process.
- FIPS Compliance: When it comes to data security, YubiKey follows strict government rules and industry standards. With the “US FIPS-140-2” compliance, it proves to be a trusted and well-known solution. This compliance ensures that the code signing process aligns with universal security standards. Moreover, it builds confidence across various industries, particularly the IT sector.
- Enhanced Security: Using code signing certificates ensures your apps’ code remains unaltered during distribution and installation. This enhances the security of your application. YubiKey, a hardware-based authentication method, securely manages the code signing certificate. This is what makes it challenging for unauthorized users to access your code. Together, they form a formidable barrier against potential cyber threats.
- Ironclad Trustworthiness: Trust is a precious commodity in a world overrun with cyber scams and impostors. Code Signing, like a stamp of authenticity, guarantees that your app is genuine. Users can install your app without second-guessing its origins. With YubiKey, this trust gets a booster shot. Users feel confident with an extra layer of hardware-backed protection. The result? Your app’s credibility skyrockets.
- Seamless User Experience: Simplicity is key in today’s fast-paced world. A code signing certificate ensures that users encounter no hitches during app installation. No alarming warnings or sketchy pop-ups—only smooth sailing. And when you add YubiKey, it takes the user experience up a notch. The hardware token is easy to use. It offers hassle-free authentication that even those without tech prowess can manage effortlessly.
- Beyond Business: Code Signing and YubiKey offer benefits not just to app developers; they extend to users as well. Consider a small business owner who relies on an app for transaction management. Through Code Signing and YubiKey, they are effectively safeguarding their business against potential security breaches. This combination ensures that only trusted and secure transactions take place, enhancing the confidence of both the business owner and their customers.
Real-World Success Stories
Achievements clearly state the impact created by combining Code Signing and YubiKey. Major players like Google, Amazon, Microsoft, Twitter, and Facebook have embraced this duo. They aid in fortifying your security landscape.
These tech titans use YubiKey devices for safeguarding employee and user accounts. This symbolizes a robust commitment to protection. But, the influence extends to password managers.
YubiKey support in these managers ushers in a new era of enhanced online security. The manufacturer, Yubico, presents the Security Key. It is a cost-effective combination equipped with FIDO2/WebAuthn and FIDO/U2F capabilities.
The outcomes have been resoundingly positive. Implementing Code Signing and YubiKey has not only minimized vulnerabilities. It has also maximized user trust. By implementing layers of security, companies have showcased their dedication to data integrity.
Reduced breaches, thwarted cyber threats, and fortified brands testify to this dynamic approach’s effectiveness. The Code Signing and YubiKey partnership is more than just a theoretical concept. It is a tangible shield that tech giants have embraced. Thus, yielding actual results that resonate across the digital sphere.
Trends and Prospects
Looking ahead, the world of cyber security is witnessing some key trends. Trends that demand robust defense mechanisms. Automotive hacking is soaring. Predictions hint at a 50 percent surge in mobile banking malware and attacks. Targeted ransomware is also on the rise. Amid these challenges is where Code Signing and YubiKey come into play.
Code Signing’s ability to verify software authenticity is becoming even more crucial. As malware grows smarter, this practice turns into a gatekeeper against tampering. Meanwhile, YubiKey, with its hardware-based authentication, ensures only authorized access. These two join forces as a formidable duo, staying ahead of emerging threats.
Embracing this security approach requires thoughtful consideration. Developers must embed Code Signing from the get-go, fortifying software against manipulations.
YubiKey’s hardware layer adds a formidable safeguard, keeping unauthorized users at bay. And what’s more, staying updated with evolving security norms is non-negotiable.
Regularly updating certificates and incorporating the latest YubiKey advancements is pivotal. In recent times, threats have been as innovative as the technology they target.
In this scenario, Code Signing and YubiKey aren’t just options. They are necessities. A blend of these measures ensures a resilient shield against a turbulent cyber environment.
In Closing
Just as a key protects your home, Code Signing and YubiKey shield your code and pieces of software. Code Signing, like a digital ID card, assures software legitimacy. YubiKey adds an ironclad layer with hardware authentication. Together, they’re an unstoppable force against cyber threats. Stay vigilant and safeguard your data. Don’t wait for trouble to knock. Choose protection. Choose Code Signing and YubiKey.


